[AWS 기본] Terraform으로 AWS 3 Tier 구성하기
1. Network 구성
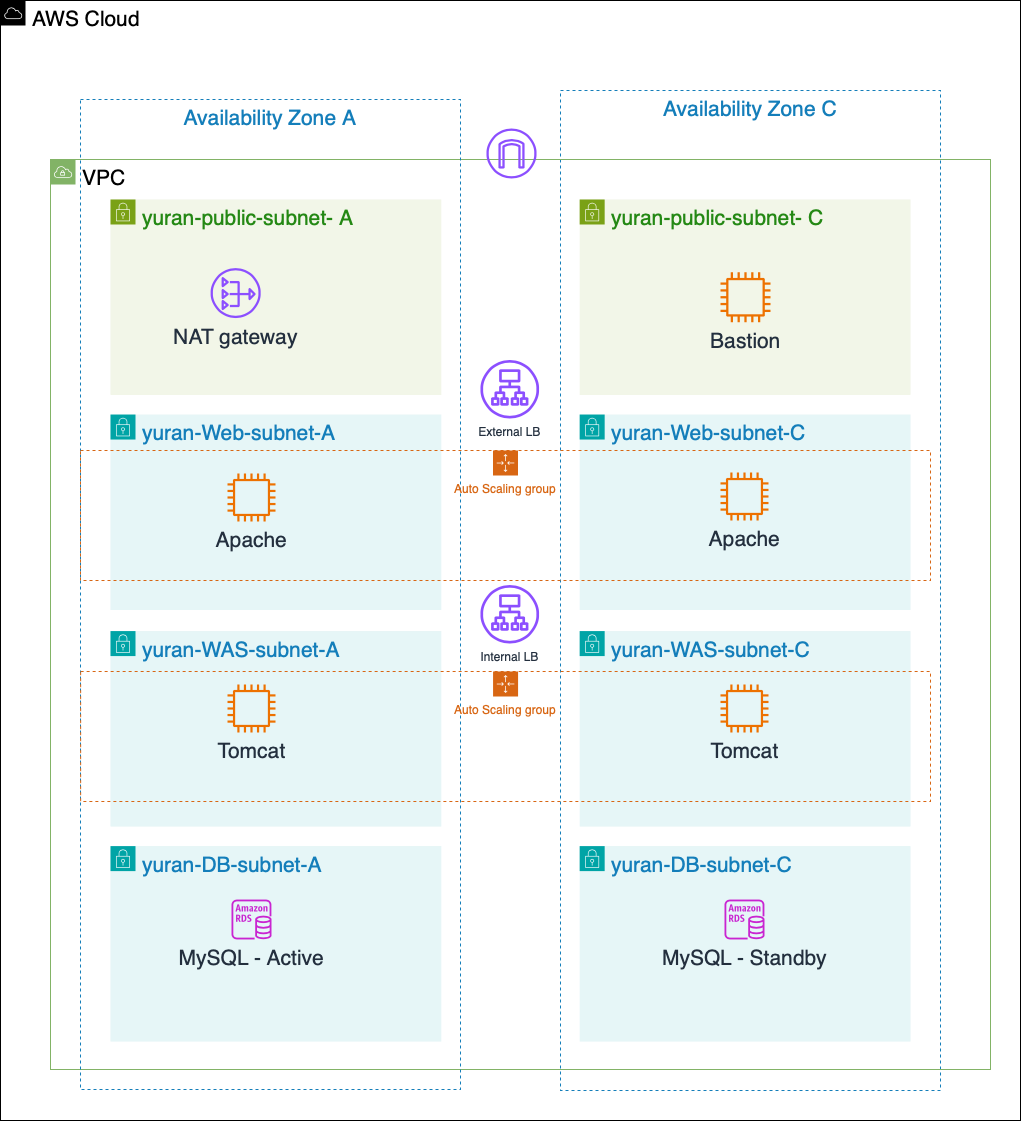
RESOURCE
| Resource | AZ | ip | tags | tags |
|---|---|---|---|---|
| 1. VPC | - | 1 | yuran-test-vpc | |
| 2. IGW | - | 1 | yuran-test-igw | |
| 3. Subnet | a | 1 | public | yuran-test-PublicSubnet-ap-northeast-2a |
| 3. Subnet | c | 1 | public | yuran-test-PublicSubnet-ap-northeast-2c |
| 3. Subnet | a | 1 | WEB | yuran-test-PrivateSubnet-0-ap-northeast-2a |
| 3. Subnet | c | 1 | WEB | yuran-test-PrivateSubnet-1-ap-northeast-2c |
| 3. Subnet | a | 1 | WAS | yuran-test-PrivateSubnet-2-ap-northeast-2a |
| 3. Subnet | c | 1 | WAS | yuran-test-PrivateSubnet-3-ap-northeast-2a |
| 3. Subnet | a | 1 | DB | yuran-test-DBSubnet-ap-northeast-2a |
| 3. Subnet | c | 1 | DB | yuran-test-DBSubnet-ap-northeast-2c |
| 4. Nat Gateway | - | 1 | public Subnet에 | natgw |
Route Table
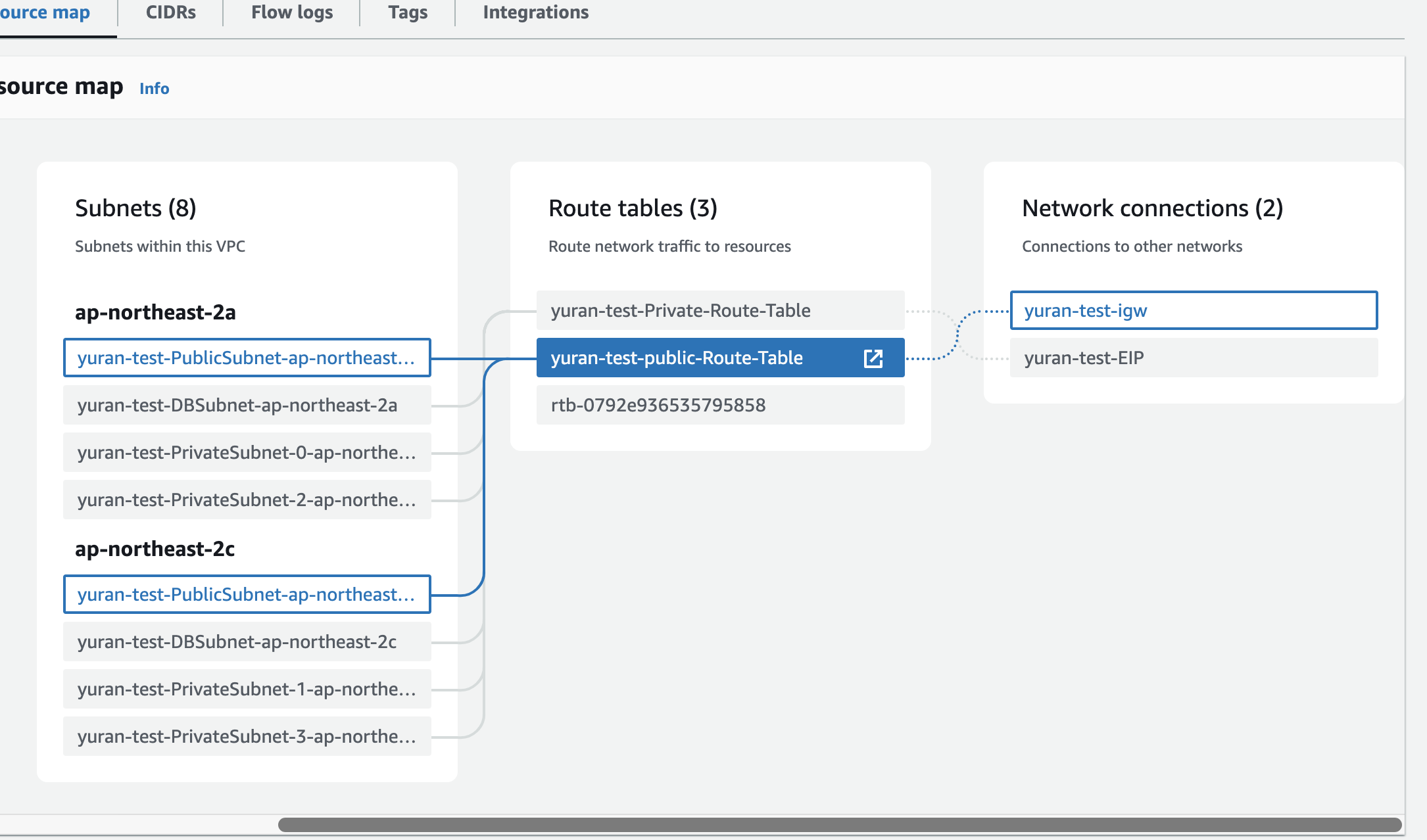

1.1 vpc
-
vpc.tf
provider "aws" { region = var.region } #1. vpc resource "aws_vpc" "yuran-test-vpc" { cidr_block = var.vpc_cidr enable_dns_support = true enable_dns_hostnames = true tags = { Name = format("%s-VPC", var.name) } }1.2 igw
-
igw.tf
#2. igw resource "aws_internet_gateway" "yuran-test-igw" { vpc_id = aws_vpc.yuran-test-vpc.id tags = { Name = format("%s-igw", var.name) } }1.3 subnets
-
subnets.tf
#3. subnets resource "aws_subnet" "public" { count = var.Desired_public_subnets vpc_id = aws_vpc.yuran-test-vpc.id cidr_block = cidrsubnet(var.vpc_cidr, 8, count.index) map_public_ip_on_launch = true availability_zone = element(var.aws_az_des, count.index) tags = { Name = format("%s-PublicSubnet-%s", var.name, element(var.aws_az_des, count.index)) } } resource "aws_subnet" "private" { count = var.Desired_private_subnets vpc_id = aws_vpc.yuran-test-vpc.id cidr_block = cidrsubnet(var.vpc_cidr, 8, count.index + 2) # map_public_ip_on_launch = true availability_zone = element(var.aws_az_des, count.index) tags = { Name = format("%s-PrivateSubnet-%s-%s", var.name, count.index, element(var.aws_az_des, count.index)) } } resource "aws_subnet" "DB" { count = var.Desired_DB_subnets vpc_id = aws_vpc.yuran-test-vpc.id cidr_block = cidrsubnet(var.vpc_cidr, 8, count.index + 6) # map_public_ip_on_launch = true availability_zone = element(var.aws_az_des, count.index) tags = { Name = format("%s-DBSubnet-%s", var.name, element(var.aws_az_des, count.index)) } }1.4 natgw
-
natgw.tf
#4. Elastic IP for NAT Gateway resource "aws_eip" "yuran-nat-eip" { domain = "vpc" } resource "aws_nat_gateway" "natgw" { allocation_id = aws_eip.yuran-nat-eip.id subnet_id = element(aws_subnet.public.*.id, 0) tags = { Name = format("%s-EIP", var.name) } }
1.5 route table
-
routable.tf
###route table ##2.1 route table for public subnets (igw) resource "aws_route_table" "public-rtb" { vpc_id = aws_vpc.yuran-test-vpc.id tags = { Name = format("%s-public-Route-Table", var.name) } } # create route for the private route table and attatch a nat gateway to it resource "aws_route" "public-rtb-route" { route_table_id = aws_route_table.public-rtb.id destination_cidr_block = "0.0.0.0/0" gateway_id = aws_internet_gateway.yuran-test-igw.id } # associate all private subnets to the private route table resource "aws_route_table_association" "public-subnets-assoc" { count = length(aws_subnet.public[*].id) subnet_id = element(aws_subnet.public[*].id, count.index) route_table_id = aws_route_table.public-rtb.id } ##4.1 route table for private subnets (natgw) resource "aws_route_table" "private-rtb" { vpc_id = aws_vpc.yuran-test-vpc.id tags = { Name = format("%s-Private-Route-Table", var.name) } } # create route for the private route table and attatch a nat gateway to it resource "aws_route" "private-rtb-route" { route_table_id = aws_route_table.private-rtb.id destination_cidr_block = "0.0.0.0/0" gateway_id = aws_nat_gateway.natgw.id } # associate all private subnets to the private route table resource "aws_route_table_association" "private-subnets-assoc" { count = length(aws_subnet.private[*].id) + length(aws_subnet.DB[*].id) subnet_id = element(concat(aws_subnet.private[*].id, aws_subnet.DB[*].id), count.index) route_table_id = aws_route_table.private-rtb.id } -
참고 문법

댓글남기기